« Back to Facilities Management Security Category Home
Cybersecurity technology considerations for electrical distribution systems
November 7, 2016
- Security
By Max Wandera
As companies steadily integrate industrial control system (ICS) devices into enterprise-wide information systems, there is an increased concern regarding cybersecurity. Today’s control systems are increasingly relying on information technology (IT) based interoperable communication technologies (TCP/IP). This exposes these systems to vulnerabilities that are typically found in computer systems and other IT networks.
While there are differences between IT systems and ICS, fundamental concepts of security like defense in depth, least privilege, access control, and segregation of duties are still applicable. In this article, we explore seven key means of defending ICS networks, relying on the above fundamental concepts and detail how facility management teams can best secure their systems.
Perimeter or boundary protection
A key consideration when securing an organization’s control systems network is protecting the perimeter. This requires the organization to clearly define the external boundaries of the control system and manage their security. A proven approach is to have a single, secure gateway to the external network.
Boundary protection technologies include firewalls, proxies, encrypted tunnels, etc. Firewalls provide the capability to add stringent and multifaceted rules for communication between various network segments and zones in an ICS network. They can be configured to block data from certain segments, while allowing the relevant and necessary data through. A thorough understanding of the devices, applications, and services that are in a network will guide the appropriate deployment and configuration of firewalls in a network.
Typical types of firewalls that can be deployed in a network include:
- Packet filter or boundary firewalls: These firewalls operate at the network layer, using pre-established rules based on port numbers and protocols to analyze the packets going into or out of a separated network. These firewalls either permit or deny passage based on these rules.
- Stateful inspection firewalls: These firewalls work at the network, session, and application layers. Stateful inspection firewalls are more secure than packet filter firewalls because they only allow packets belonging to allowed sessions. These firewalls can authenticate users when a session is established and analyze a packet to determine whether they contain the expected payload type or enforce constraints at the application layer.
- Application-level proxy firewalls: These firewalls are highly secure firewall protection methods that hide and protect individual devices and computers in a control network. These firewalls communicate at the application layer and can provide better inspection capabilities. Because they collect extensive log data, application-level proxy firewalls can negatively impact the performance of an ICS network.
- Host firewalls: These firewalls are software firewall solutions that protect ports and services on devices. Host firewalls can apply rules that track, allow, or deny incoming and outgoing traffic on the device and are mainly found on mobile devices, laptops, and desktops that can be easily connected to an ICS.
- SCADA hardware firewalls: These are hardware-based firewalls that provide defense for an ICS based on observing abnormal behavior on a device within the control network. For example, if an operator station computer suddenly attempts to program a PLC, this activity could be blocked and an alarm could be raised to prevent damage to the system.
Network segmentation
Network segmentation is a key consideration in establishing secure control networks. Firewalls should be used to create demilitarized zones (DMZ) by grouping critical components and isolating them from the traditional business IT network and other non-critical control systems. Three-tier architecture should be employed at a minimum, with a DMZ between the organization’s core network and an isolated control system’s network as shown in the graphic.
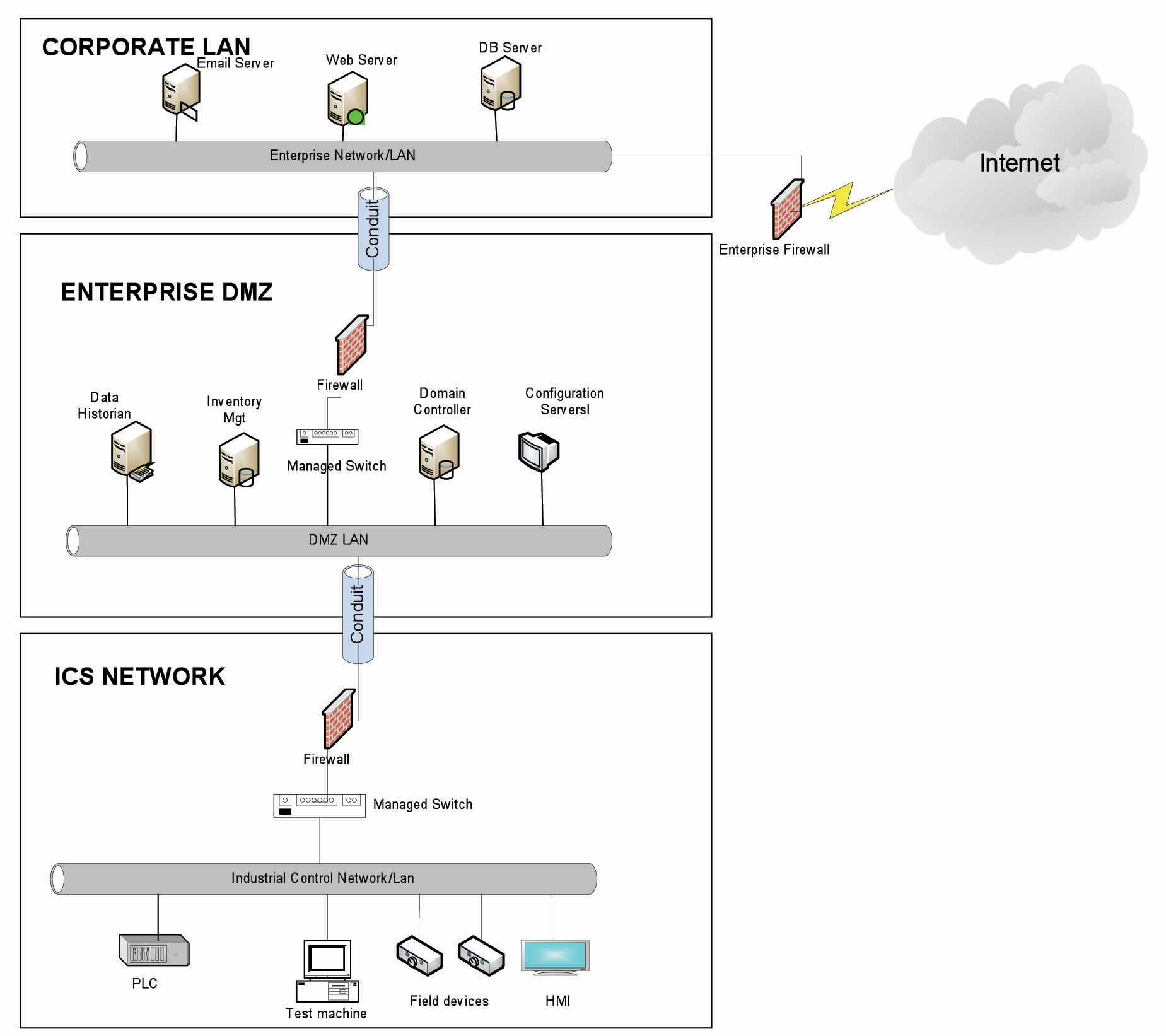
The graphic shows that the network can be divided into layers or zones based on functions, and then connected by conduit, or connections between the zones, that provide security controls to:
- Control access to zones
- Resist denial of services attacks or the transfer of malware
- Shield other network systems
- Protect the integrity and the confidentiality of network traffic
Access control, both physical and logical, is a key consideration within the realm of network segmentation. The key consideration when designing access control is defining the required interactions both within a given zone and between zones. These interactions should be mapped out clearly and prioritized based on need. It is important to realize that every hole poked in a firewall, increases potential exposure to attacks.
Intrusion detection and prevention
Intrusion detection and prevention is the process of identifying possible incidents in an ICS network, logging the information about them, attempting to stop them, and reporting them to ICS security administrators. The type of intrusion detection and protection system (IDPS) technology deployed will vary with the type of events that need to be monitored. There are four classes of IDPS technology:
- Network-based IDPS monitors network traffic for particular ICS network segments or devices and analyzes the network and application protocol activity to identify suspicious activity
- Wireless IDPS monitors and analyzes wireless network traffic to identify suspicious activity involving the ICS wireless network protocol
- Network behavior analysis IDPS examines ICS network traffic to identify threats that generate unusual traffic flows such as DOS attacks
- Host-based IDPS monitors the characteristics and the events occurring within a single ICS network host for suspicious activity
Owing to the critical nature of operations in control networks, ideal approach is to first introduce an intrusion detection system (IDS) to passively listen to the network traffic and report potential security issues. Introducing an active inline intrusion prevention system (IPS) into control network is a very critical decision and should be taken only after gaining enough confidence on the detection capabilities
Because IDPS systems are critical in an ICS network, they become regular targets for attacks and securing them is also extremely important. Another important consideration when deploying IDPS systems is that they don’t adversely impact the performance of the ICS network.
Continuous monitoring and incident response
It is important to understand what is happening within the network from both a performance and security perspective. This is especially true in a control systems environment. Log and event management entails monitoring infrastructure components such as routers, firewalls, and IDS/IPS, as well as host assets. Security information and Event Management (SIEM) systems can collect events from various sources and provide correlation and alerts. Having the capability of generating and collecting events, or even implementing a SIEM is not sufficient by itself.
It is paramount for the organization to have the capacity in terms of resources (personnel, processes, tools, expertise) needed to perform meaningful interpretation of the information and initiate timely and appropriate response in case an incident is suspected. Through monitoring, the organization can identify issues such as suspicious or malicious activities. Awareness can be raised when new (potentially unauthorized) devices appear in the environment. Also the organization needs have a functional feedback process in place in order to reduce the false positive calls when infrastructure changes happen. Careful consideration should be taken into account to ensure that log and event management does not adversely impact the functionality or the reliability of the control system devices.
ICS hardening
Defense-in-depth is a strategy of establishing variable barriers across multiple layers in an organization. After deploying electronic countermeasures such as firewalls, intrusion detection software/components, continuous monitoring, it is important to harden the ICS to be resilient to malicious attacks even if other defenses are breached.
The goal for system hardening is to reduce as many security risks as possible by securely configuring IC networks and systems. The idea is to establish configurations based on what is required and eliminate unnecessary services and applications that could potentially provide another possible entry point to an intruder.
Minimum security baselines should be established for the various platforms and products deployed (operating system, application, and infrastructure elements such as drives, meters and human machine interface (HMI) devices). The following actions should be implemented where applicable:
- Change default passwords
- Disable unnecessary services
- Disable anonymous access to network services, for example, file transfer protocol (FTP)
- Do not use clear text protocols (for example, use Secure Shell (SSH) v2 instead of Telnet)
- Install only required packages, applications, and features
- Deploy antivirus solutions where possible
- Disable or otherwise control use of USB devices
- Establish a warning banner
It may be easier to implement these actions on devices for which you control the base operating system platform. However, several of the items listed above can be configured from the product specific configuration options. Changes such as these could potentially impact the functionality of a control system device. Extensive testing needs to be conducted before deployment to minimize this impact.
Patch management planning and procedures
A patching and vulnerability management process should be established based on the timely awareness of issues and appropriate action. This process should take all of the elements that make up the control system environment into consideration.
Information resources should be identified for vulnerability and advisory information for the various components in the environment. These should include vendor-specific sources as well as other public or commercial services that provide vulnerability advisory information. For example, the National Vulnerability Database provides information related to vulnerabilities identified in general IT components, while the Industrial Control Systems Cyber Emergency Response Team publishes advisories specific to control systems.
A regular patch deployment schedule should be established for each component in the environment. Depending on the component, this could range from a monthly schedule to an as-needed deployment, depending on the historical frequency of patch or vulnerability related issues for the component or the vendor. Additionally, out-of-band or emergency patch management needs to be considered and qualifications need to be defined.
Vulnerability information and advisories should be reviewed regularly and assessments should be performed to determine the relative severity and urgency of issues. Elements of the process should also include the preparation, scheduling, and change controls; testing and rollback procedures; and pre-deployment notification to stakeholders that includes scope, expectations, and reporting.
In context of ICS networks, testing is a significant element, as the effect of the patch application needs to be clearly understood; unintended or unexpected impacts to a control system component influence the decision to deploy a patch. In the event that it is determined that a patch cannot be safely deployed but the severity of the issue represents a significant concern, compensating controls should be investigated and deployed.
Continuous assessment
Ongoing vulnerability assessments are critical to identify issues and understand the effectiveness of other defensible network elements. Assessments should include testing and validating the following:
- Device configuration of services and applications
- Monitoring capabilities and alerts are triggered and responded to as expected
- Expected connectivity / restrictions within and between zones
- Existence of previously unknown vulnerabilities in the environment
- Effectiveness of patching
A program should be established for performing assessments. The actual assessment should be performed by a qualified resource, which can be an in-house or third-party organization. Regardless of who performs the assessments, in-house resources need to be involved in the planning, scoping, and supporting of assessment activities and must be appropriately trained to do so.
Assessments should be conducted according to a methodology that is clearly defined to address:
- Physical security
- People and processes
- Network security
- Host security
Running of automated tools for network discovery and vulnerability assessments is highly sensitive in ICS context. There is always a potential of bringing down the network if the penetration testers are not aware of ICS context and run such tools with unsafe options. Therefore, penetration testing methodologies used for an ICS network must be thoroughly tested beforehand.
To protect important assets, all organizations must take cybersecurity threats seriously and be proactive with a system-wide, defense in depth approach specific to organizational needs.
While there is no foolproof method to complete security, following the seven identified technology practices will greatly limit the potential exploitation of vulnerabilities.
It is critical ICS administrators remain aware of changes in the cybersecurity landscape and continue to work to prevent potential vulnerabilities in the systems they manage.
To learn more, visit Eaton.com/cybersecurity.
Max Wandera is the director — global products cybersecurity center of excellence at Eaton.








