How To Evaluate Facility Security Vulnerabilities
Any criminal or malevolent activity requires desire, ability, and opportunity.
Just as every facility is unique, so are its security vulnerabilities. However, these are not static challenges. Those who would seek to gain unauthorized access to a facility and wreak havoc of one kind or another are constantly dreaming up ways to overcome whatever security measures a facility might already have in place. In addition, complacency could create avoidable vulnerabilities that will be easy to exploit. It is important for facility managers to truly understand their facilities' potential vulnerabilities and the likelihood of an incident occurring.
Why bad things happen
Any criminal or malevolent activity requires three elements: desire, opportunity, and ability.
Desire — Desire in this context indicates inquisitiveness, greed, or emotions. Inquisitiveness and emotions represent the bigger concerns, because they will provide more motivation to commit the act.
Ability — Certainly, the availability of the tools needed (lockpick, pry tools, computers, knowledge) is a paramount concern. How easy it is to obtain the tools, and the degree of knowledge required to commit the act, will influence the aggressor’s decision to conduct an attack.
Opportunity — This represents the time frame to commit the act and speaks to the potential for the aggressor to be detected or to remain anonymous. Opportunity exists when a police or security officer is distracted or the number of controls in place is limited. Opportunity is the only aspect of this cycle that we can leverage to prevent a criminal act from occurring.
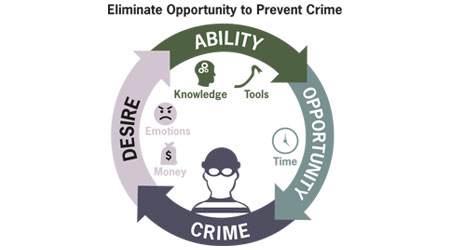
(Any criminal or malevolent activity requires desire, opportunity, and ability. Facility managers can prevent crime by removing opportunity from the cycle. Source: Affiliated Engineers Inc.)
While desire paired with ability and opportunity describes the criminal cycle, there are two subsets of criminal activity that influence the success of an aggressor. These are opportunistic aggressor and a determined attacker. An opportunistic aggressor is one that will commit an act at a specific time without any pre-planning, making a rational choice of risk versus reward in seconds before committing the act. A determined attacker will have a greater impact and is more likely to be successful because the pre-planning/reconnaissance and tools will be more robust. Thus, the more prevalent the desire or tools, the more likely an event.
Probability and impact
The three elements just described are not the whole story. To understand the risk for occurrence, we need to understand impact compared to the controls or defenses that are in place. This is the fundamental aspect of security that is so daunting, because many are of the "it won't happen to us" mind-set.
Impact in the broadest sense of the term is the measurement of the effects of an incident and the speed with which the organization can recover. For instance, a security incident at an individual facility will certainly have an impact/effect on that single company. However, if that company is a large telecommunications, electricity, or water provider, the impact would be greater. An analysis allows us to make a risk decision on what programs we will invest in to defend against a hypothetical threat.
Related Topics:















