Security Risk Assessment Shows Where Security Dollars Are Best Spent
First of a two-part article explaining the importance of early planning and security risk assessments for mitigating threats.
A security risk assessment is the eyes-wide-open approach to designing safer, more secure buildings. When performed in the concept design phase of a new building or significant renovation or expansion, the security risk assessment generates a detailed document that informs the design of building architecture and systems. The assessment analyzes threats to the specific assets of the project and vulnerabilities in design that could allow the threats and their consequences to occur. The assessment also proposes high-level, conceptual mitigation strategies to implement in the architectural, structural, mechanical, electrical, plumbing, and security systems. When implemented in the early design phases, the cost and aesthetic impacts on the project can be minimized.
While every assessment is project-specific, almost all buildings have certain fundamental critical assets — the people who live or work in or visit the facility and the electrical, mechanical, and IT infrastructures — that are always included. Other facility-specific critical assets are identified by the owner and other key stakeholders that, if lost, would significantly impact the ability to operate the facility, owner’s business, tenants’ businesses or residents’ homes, for example, significant impairment of a financial institution’s IT infrastructure.
Communication with key stakeholders is fundamental to developing and validating the security risk assessment. Typically, four key stakeholders are at the table: the project client, which may be an architectural firm or owner, depending on which entity has contracted for the assessment; the ultimate owner of the project; project manager; and the operator of the project, which may be the in-house building operations manager or a third party. Together they will identify for the security risk assessment consultant the goal of the project, type of property, location, and whether or not it will be an iconic building. If the assessment is conducted early in the project, it often is too early to have identified the property’s security contractor, tenants, and security products. Therefore, the analysis focuses largely on the design, but offers high-level advice for the client to follow over the course of the project. The security risk assessment also will engage local building authorities, utility providers, first responders, and government entities, where applicable.
Just as all facilities have common and unique critical assets, the same can be said of threats, which may range from commonplace thefts and minor acts of vandalism to a terrorist attack on an iconic institutional building.
The assessment is informed by statistical analyses of the likelihood of certain threats occurring in particular geographic locations and types of facilities. Third-party analyses and statistics can be used to determine the likelihood of a certain threat in a given location and facility. Security risk assessment consultants may also use their own proprietary methods of determining the threat level. Often, the analysis will contain elements from both methods.
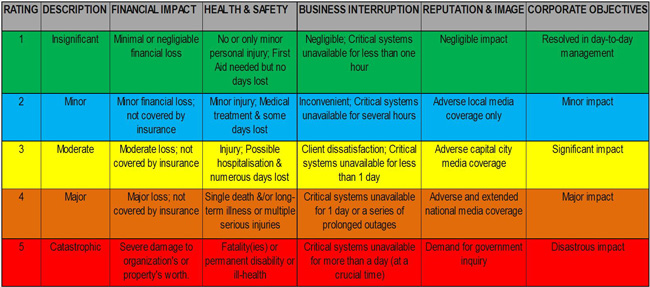
Vulnerabilities — the shortcomings in design that could allow any of the threats to occur — are unique to each project, as are consequences. The owner must evaluate the specific potential consequences and assess the operational and financial impacts in each case, which may range from “insignificant” to “catastrophic.”
Mitigating risks
The security risk assessment prioritizes the threats and vulnerabilities and identifies design strategies to mitigate these. From there, the security risk assessment may produce some high-level advice on cost impact regarding these strategies. The owner can use this document to weigh its risk appetite and make decisions about the cost-benefit of the various means to mitigate the risks, including the recommended design strategies, as well as operational strategies or insurance solutions. An owner may also decide to accept any or all of the risks in full. Based on discussion, the security risk assessment consultant will make specific recommendations and work with the project manager and his or her liaisons for the various building systems to implement appropriate changes to the design.
The security risk assessment analyzes all risks, threats and vulnerabilities from the outside in, proceeding in a series of concentric circles including the surrounding geographic area, district (business, residential, industrial, or institutional), adjacent properties, building site, and the building itself from the perimeter to the interior and each of its major infrastructure systems. Moreover, the assessment will draw on incidents occurring at similar sites in other areas.
The analysis of the architectural systems focuses on the degree to which common threats are mitigated through basic strategies such as design of clear entry and egress paths, clear delineation between public and private areas, clear sight-lines for building operators and managers, and clear means of identifying the presence of individuals in unauthorized areas. Facade design concepts are also assessed. The analysis may include secure zones for unique critical assets, such as documents, currency, cultural artifacts, and art works.
Similarly, the designs of the structural, mechanical, electrical, and IT infrastructure systems are assessed. These analyses fundamentally look at system access, operating controls, and continuity. For example, the assessment identifies access points for utility power, which may be points of vulnerability for a threat occurring within or outside the property line, including potential sabotage from remote locations.
Other analyses may be performed, based on a full CAD or BIM model. For example, a blast analysis may be performed using computer modeling to assess the impact of a blast from a human- or vehicle-carried explosive device on the structure. An HVAC particle dispersion analysis, while less commonly performed than a blast analysis, uses computer modeling to assess the impact on the building if the air distribution system were to be used to disperse a noxious or toxic agent.
Mitigation strategies are offered in increasing detail at each step of design in coordination with the design disciplines and construction trades. After recommendations are incorporated into the design, the revised design is assessed for impact on risks. There is continual engagement with stakeholders to address new threats and vulnerabilities that may arise.
Related Topics:














