Steps To Take To Improve BAS Cybersecurity
Part 3 of a 4-part cover story on cybersecurity and the BAS.
In the past, systems integrators often installed older BAS without even the most basic IT protections, such as firewalls, and used default log-in credentials, according to Chipley. Even some new systems are still using weak protections, he says. “The software on these automated devices does really neat things,” Rios says, “but the security is just really poor, and we’ve been telling people this for the longest time. The common best practices we find in the security industry are just not used by these building automation devices. Every time we’re asked to basically penetrate a building automation system and do things with it, we’re always successful. There’s never been an engagement where we’ve failed. That’s pretty sad.”
Referring to the pivot a successful BAS hacker can sometimes make into an entire company network, he says, “I don’t think I can remember a time we failed to pivot from the automation network to the corporation network. A lot of folks will say, ‘Hey, we’re segmented, we’re separated,’ and a lot of times those comments are based on pretty naïve assumptions about the way these systems work. You probably have a lot more integration points than you realize.”
What is important is to audit whether you really have separation, and that’s harder than you think, Rios says. “People re-use passwords, people re-use accounts, people have VPN (virtual private network) tunnels back and forth between these different environments, people are passing data around all the time. If you think segmenting these systems off corporate networks is very simple, you’re fooling yourselves. We’ve demonstrated that time and time again.”
How We Got To This Point
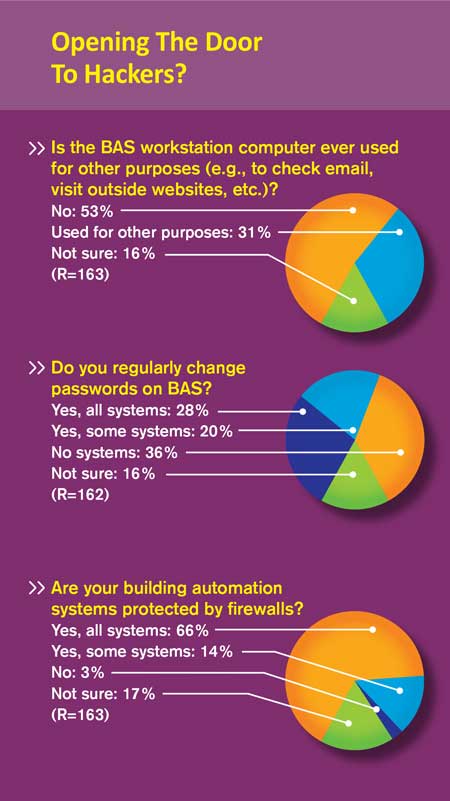 Although BAS vulnerability may partly be due to complacency on the part of facility operators, habit and history also help explain it. Most facilities, Chipley says, lack a culture of doing normal maintenance of patches (software fixes for security and other flaws), performing continuous monitoring, and conducting monthly security audits. And back in the day, there was never a requirement to even secure building control systems and enforce protocols. Zimmer mentions a speaker at a CABA conference who described a company that had gone to enormous lengths to secure its computer system. Yet a single employee brought in a memory stick he had been using at home, plugged it in to use work documents, and unintentionally infected the IT network with malware.
Although BAS vulnerability may partly be due to complacency on the part of facility operators, habit and history also help explain it. Most facilities, Chipley says, lack a culture of doing normal maintenance of patches (software fixes for security and other flaws), performing continuous monitoring, and conducting monthly security audits. And back in the day, there was never a requirement to even secure building control systems and enforce protocols. Zimmer mentions a speaker at a CABA conference who described a company that had gone to enormous lengths to secure its computer system. Yet a single employee brought in a memory stick he had been using at home, plugged it in to use work documents, and unintentionally infected the IT network with malware.
Shircliff believes the true cybersecurity problem is with existing building stock, not with smart buildings. “With smart buildings, you’re at least having the conversation about how something is connected with IT and who is responsible and how it works,” he says. “But for decades, people have been just plopping in servers with a DSL line and just going home, with no conversation about this. It’s the existing building stock that is our Achilles heel in the industry.”
A lot of control devices were never meant to be connected, and the connectivity has been “bolted on” after the fact, says Rios, basing his comment on having taken the devices apart for analysis. “There’s often no way to centrally manage a lot of these devices either. This is the plight of many facility managers — they have 20 different pieces of software to run their devices. To change the passwords for all your devices on a regular basis is kind of a pain for facility folks, and because it’s such a pain, they don’t do it.”
Steps Facility Managers Can Take
The first step in improving building control cybersecurity is to determine what you have, and then move on to basic fixes, Shircliff says. Inventory what is in your mechanical rooms and who’s maintaining it. What is the control system and its vintage? What’s the current software/firmware level? Is there a password custody policy? Are there any vendor policies relating to cyber security at all? What are the internal company policies? What are the threats?
The path to improvement starts simply enough. Put in basic firewalls and make sure all servers, workstations, and laptops have strong user names and passwords, and that all users get their own. Don’t use common passwords everyone knows. If someone uses the same password on both the BAS and corporate network, that could give hackers an opening. (Rios says his team once assessed 100 different BAS configuration files and about 12 percent had no password at all.)
Don’t give vendors unfettered access to your system, because they could unwittingly give away access, Gordy says. Implement a password protocol for the controls contractor requiring that the system owner be notified when an employee (especially a disgruntled one) is no longer with the contractor. The BAS owner should fully control access and users, not the controls vendor — which is too often the case, Gordy says. Access should be on an “as needed” basis.
Systems sitting out on a public IP (Internet Protocol) are not behind a firewall and are relatively exposed, Gordy says. The better way to provide remote access to a control system, he says, is to put it behind the firewall and have qualified IT personnel set up a hardened VPN (virtual private network).
Making sure all your BAS are patched would go a long way to improving security, and is not a big undertaking, Rios says. Few systems are running the latest version of software and firmware, he adds. A caution: Trying to patch known security leaks can potentially trigger automatic system-scanning software into shutting down important components or technology that are vital to facility function. So conduct a systematic diagnosis before deploying patches on an aging network.
For Chipley, the first step toward improved security is to create a building control system enclave — a section segregated from the rest of the network — and separate IT systems from operational technologies (OT) systems. That means putting them into “demilitarized zones” (DMZs), or separate, segmented VLANs (virtual local area networks). This restricts the ability of hackers to access internal servers and data via the Internet. “You can still have one fiber, but two VLAN pipes inside — one for IT, one for OT — that aren’t exchanging data,” he says. “Similarly, you don’t use the same workstation for managing your OT systems as managing your IT systems.”
Chipley suggests replacing Internet access with a virtual private network that requires use of multi-factor tokens, which provides authentication of a user’s identity into the network first, and then into the laptop or work station running the BAS software. In addition, he advises locking mechanical, electrical, and pump rooms; using CCTV monitoring; and restricting access to building controls and devices.
Despite great protections, a third-party provider — for example, a contractor bringing in an infected laptop — can still ruin everything. The U.S. Defense Department not only segments networks, but requires maintenance contractors to have a government-issued laptop scanned before they’re allowed to install their service packs and connect to the network, and then scanned again on the way out, Chipley says.
David Fisk, a professor of systems engineering and innovation at Imperial College in London, takes a different tack. Assume you’ll be hacked, he suggests, and design a recovery plan that covers the five to 10 days it might take to clean up your system.
What might improve the quality of cybersecurity precautions, he adds, “is the need for the firm to take out cyber attack insurance. Because insurers are being asked to cover losses in the order of millions of (dollars), they expect their clients to have an accredited level of security. The IT industry is beginning to wake up to the implications of a networked BMS. Expect some spring cleaning of passwords and access protocols!”
At the end of the day, Gordy says, the biggest vulnerability for a facility is its people. You can put up all the walls you want, he says, but if someone accidentally opens a door, you can’t stop an intruder.
Send questions and comments to ronald.kovach@tradepress.com.
Related Topics:









 Although BAS vulnerability may partly be due to complacency on the part of facility operators, habit and history also help explain it. Most facilities, Chipley says, lack a culture of doing normal maintenance of patches (software fixes for security and other flaws), performing continuous monitoring, and conducting monthly security audits. And back in the day, there was never a requirement to even secure building control systems and enforce protocols. Zimmer mentions a speaker at a CABA conference who described a company that had gone to enormous lengths to secure its computer system. Yet a single employee brought in a memory stick he had been using at home, plugged it in to use work documents, and unintentionally infected the IT network with malware.
Although BAS vulnerability may partly be due to complacency on the part of facility operators, habit and history also help explain it. Most facilities, Chipley says, lack a culture of doing normal maintenance of patches (software fixes for security and other flaws), performing continuous monitoring, and conducting monthly security audits. And back in the day, there was never a requirement to even secure building control systems and enforce protocols. Zimmer mentions a speaker at a CABA conference who described a company that had gone to enormous lengths to secure its computer system. Yet a single employee brought in a memory stick he had been using at home, plugged it in to use work documents, and unintentionally infected the IT network with malware.

